Setting Up SAML Authentication with Azure AD
- Create Application in Azure Portal: Begin by navigating to the Azure Portal and creating a new application named "Kibana login with Azure AD" under the Azure AD service.
- Enable SAML Authentication in OpenSearch: Access the AWS console, go to the OpenSearch service, and navigate to Actions > Modify authentication. Enable SAML authentication and input the Service Provider Entity ID & SP-initiated SSO URL obtained from Azure AD.
- Configure Single Sign-On in Azure AD: Edit the Single Sign-On settings of the Enterprise application in Azure AD. Add the OpenSearch Service Provider Entity ID as the Identifier (Entity ID) and the SP-initiated SSO URL as the Reply URL.
- Assign Users/Groups: Specify the users or groups in Azure AD who should have access to the Enterprise application. These will later be mapped to roles in Kibana.
- Define User Attributes & Claims: Configure Azure AD to send group information to OpenSearch as attributes to streamline role mapping.
- Download Federation Metadata XML: Download the metadata XML file from Azure AD.
- Upload Metadata in OpenSearch: Upload the XML file in OpenSearch SAML configuration through the AWS console.
- Apply SAML Integration: Update Terraform configuration to reflect SAML integration changes and apply them.
Mapping Roles in Kibana
- Login with Master User: Gain access to the Kibana dashboard using master user credentials.
- Map User Email to Roles: Map user email IDs to OpenSearch dashboard user roles to grant appropriate access levels.
Addressing Challenges: Role Mapping and Permissions
During the implementation of SAML authentication with Azure AD on OpenSearch, we encountered and resolved some challenges to ensure smooth user authentication and access control.
Role Mapping Challenge:
Ensuring that users logging in via SAML were correctly mapped to the corresponding roles within Kibana posed a challenge initially, resulting in access errors.
Solution: Mapping Users to Roles
We implemented a systematic approach to map users to specific roles within OpenSearch. This involved associating users or groups from Azure AD with predefined roles in OpenSearch to ensure proper access levels based on organizational roles.
Permissions Management:
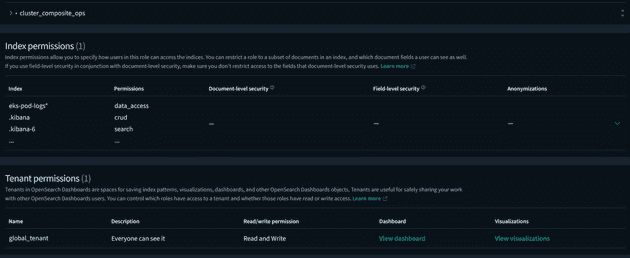
Users encountered permission errors when attempting to save queries or dashboards within Kibana due to insufficient permissions on essential indices such as .kibana.
Solution: Granting Index Permissions
To address this, we configured permissions on relevant indices within OpenSearch, including .kibana, allowing users to save queries, visualizations, and dashboards seamlessly.
By overcoming these challenges, we established a robust SAML authentication mechanism with Azure AD in OpenSearch, ensuring secure and efficient access control for users.
Conclusion
In conclusion, configuring SAML authentication with Azure AD in OpenSearch is a pivotal step towards enhancing both the security and usability of log management systems. By seamlessly integrating these technologies, organizations can ensure secure access to critical data while streamlining user authentication processes. Despite encountering challenges such as role mapping and permissions management, our systematic approach and solutions have paved the way for a robust authentication framework. Through diligent implementation and continuous refinement, organizations can leverage the power of SAML authentication to bolster their security posture and facilitate efficient log management practices.